Public Proxy Servers : User Guide For Beginners
One of the popular techniques to mask IP address or conceal IP address to surf anonymously is to utilize a proxy server which comes in one form or another. A proxy server is a server computer allow its users to make indirect network connections to other network services in this case the internet while hiding your online identities. The proxy provides the resource either by connecting to the designated server or by serving it from a cache. There are various implementations of proxy servers that you can use to hide your IP address i to stay anonymous online
Web-based Proxy Servers
A web-based proxy server is a website that provides a field for you to input the URL of a website that you wish to surf anonymously as shown in the picture bellow . When you submit the form the web-based proxy server makes a request for the page that you want to visit.
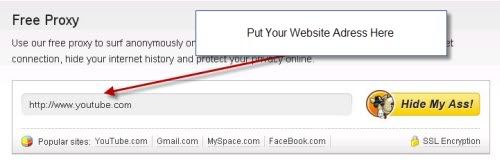
The machine typically doesn’t identify itself as a proxy server and doesn’t pass along your IP address when requesting for the page you wish to visit. The features of these web sites vary (ad blocking, javascript blocking, etc) as does their price. Some are free of charge and some are paid services. Examples of web-based proxy services are: Proxify.com, hidemyass.com, freeproxyserver.net and many more.
Mask IP Address with Browser-Configured Proxy Servers
In addition there are also stand alone proxy servers that allow you to configure your browser to route your browser traffic through them ,after which the servers makes a request for a page on your behalf, and then sends you the results. You can find public proxy server by typing the sentence “proxy list” on search engines’ search box. One such site that provide fresh public proxy list on a daily basis is proxy-list.org . Bellow is the screenshot from proxy-list org :
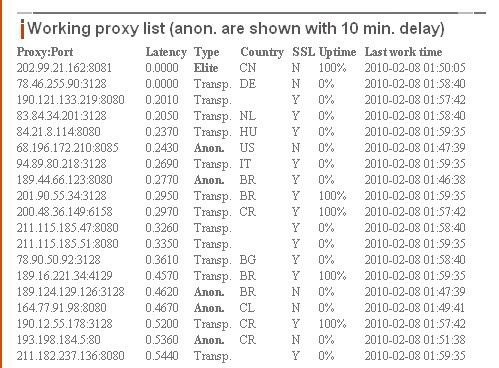
Because web-based proxies are mostly available to the public for free, you may not expect too much in terms of its speed reliability except you subscribe to the paid services.
Public Proxy servers are in general divided into three categories:
- Transparent Proxy – This type of proxy server makes the original IP address available via the http headers. These are normally utilized because of their ability to cache websites but don’t provide reliable anonymity to those using them. Yet a transparent proxy will get you around simple IP bans or get around web filter at workplace or schools. They are transparent in the terms that your IP address is disclosed , not transparent in the terms that you don’t know that you are using it.
- Anonymous Proxy - This type of proxy server identifies itself as a proxy server, but doesn’t make the original IP address available. This type of pr provides reliable anonymity for most users and hides your IP address. Distorting Proxy – This type of proxy server identifies itself as a proxy server, but make an false original IP address available through the http headers and conceals your real IP address.
- High Anonymity Proxy – This kind of proxy server doesn’t make available the original IP address and hide your IP address entirely
The risk Of using anonymous proxy servers
In using a proxy server, all information transferred to the service being used must pass across the proxy server before being sent to the service, mostly unencrypted . It’s consequently possible, and has been attested, for a malicious proxy server to snoop upon everything sent to the proxy: including unencrypted logins and passwords. By chaining proxies which don’t divulge information about the origin of requester, it is possible to obfuscate activities from the eyes of the user’s destination. Still, your footprint will be left on the intermediate hops, which could be exploited . If the policies and administrators of these other proxies are unidentified, the users may fall victim to a security fallacy . The bottom line of this is to be cautious when connecting to proxy servers hide your real IP address, and only use familiar and respectable proxy servers , and never use proxy servers of questionable reputation. Whenever there is no choice but to use obscure proxy servers, don’t pass any confidential information unless it is properly encrypted. So that instead of masking your Identities by using their services to conceal your IP Address you expose your vital information to cyber criminals.